People are the weakest link in all computer systems. We hear about the best cryptography money can buy: integrity checking,
Continue reading
| fascinated by how people use technology & vice-versa…

People are the weakest link in all computer systems. We hear about the best cryptography money can buy: integrity checking,
Continue reading
Humans are involved in 80-90% of IT security system breaches. We have the technological capacity to keep our software systems
Continue reading
In the above picture a newbie gamer has organised a telephone for his Sim so that it can order pizza.
Continue reading
[update 20/8/20: My guide to human-computer interaction is now available over on Udemy.] The recent furore over the 2012 Olympics Logo reminds
Continue reading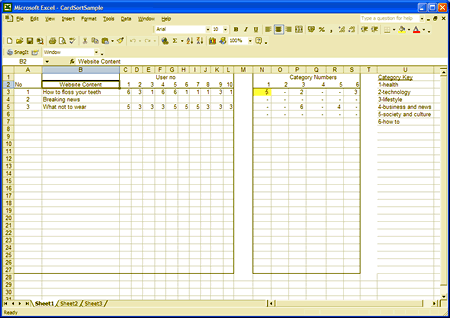
Card sorts are an easy way to see if the current architecture of a website is working. They encourage users
Continue reading